October 3, 2018 | Monograph
Kim Jong Un’s ‘All-Purpose Sword’
North Korean Cyber-Enabled Economic Warfare
October 3, 2018 | Monograph
Kim Jong Un’s ‘All-Purpose Sword’
North Korean Cyber-Enabled Economic Warfare
Executive Summary
North Korea pledged to “cease all hostile acts … in every domain” as part of the Panmunjom Declaration, which Kim Jong Un and South Korean President Moon Jae In signed in April. 1 When Kim met U.S. President Donald Trump in June, the North Korean leader committed to “build a lasting and stable peace.”2Yet, even as diplomacy proceeded at the highest levels, Pyongyang continued to engage in cyber attacks against the national security and economic base of South Korea.3 Experts estimate that South Korea suffers as many as 1.5 million attempted cyber intrusions from North Korean hackers every day.4 Pyongyang uses cyber tools to support “active measures” and spread disinformation to sow division in South Korean society, and to undermine the Republic of Korea (ROK) government. 5
The heavily sanctioned and cash-strapped North also uses cyber attacks to generate illicit funds from ransom payments,6 cryptocurrency exchange hacks, 7 and fraudulent inter-bank transfer orders.8 Cyber espionage has provided the regime with critical intelligence on its adversaries.9 In September 2018, the Department of Justice pressed charges against a North Korean computer programmer, Park Jin Hyok, for not only working on behalf of the North Korean government, but also being involved in several infamous North Korean cyber operations such as the Sony Pictures hack, SWIFT Bangladesh Bank theft, and WannaCry, which will all be discussed in this report. 10 Attribution is often a tricky endeavor. 11 Yet, the Justice Department presents comprehensive evidence based on forensic technical analysis that link these major North Korean cyber intrusions back to Park.12 This not only paints a clearer portrait of the Kim regime, but also the diverse range of offensive cyber capabilities Pyongyang employs.
While Kim Jong Un’s nuclear and missile arsenal present the most extreme threat, both the U.S. and ROK should take note of North Korea’s growing cyber capabilities. These capabilities complement North Korea’s conventional and unconventional military weapons in a highly effective manner. North Korea’s cyber operations broaden the Kim family regime’s toolkit for threatening the military, economic, and even the political strength of its adversaries and enemies.
Within the cyber domain, the United States and its allies should pay special attention to the emerging threat of cyber-enabled economic warfare (CEEW), or cyber attacks against an adversary “to weaken its economy and thereby reduce its political and military power.” 13 CEEW attacks could compromise the networks of financial institutions, banks, and corporations that play an indispensable role in the nation’s economy. Sustained or expanded North Korean cyber attacks on the critical infrastructure and economies of South Korea, the U.S., and other nations could threaten the foundation of their power. Even more insidious is how such cyber attacks, or even the threat of them, may change the policy calculus of dealing with North Korea going forward. Essentially, North Korea could hold military and diplomatic policy hostage by putting a country’s industrial, financial, or energy sectors in its cyber cross hairs.
Although North Korea’s cyber capabilities still cannot match those of Russia, China, and the U.S., they have improved substantially. Our case studies of six North Korean attacks show how their offensive tactics have evolved from basic distributed denial of service (DDoS) attacks to sophisticated use of malware. In 2013, the world witnessed the DarkSeoul attacks in South Korea in which Pyongyang first demonstrated its ability to inflict physical damage through cyber-enabled means against South Korean banks and media companies. A little over a year later, in November 2014, Pyongyang used these destructive capabilities against U.S.-based Sony Pictures. North Korea’s cyber infiltration of more than a hundred private South Korea firms and government agencies between 2014 and 2016 foreshadows the battles to come. 14
The case studies in this report are not all explicit examples of CEEW operations. However, each of has significant implications for the future of CEEW. As diplomatic efforts to dismantle North Korea’s nuclear weapons program move forward – or even if they do not – the flexibility and plausible deniability of cyber capabilities may make them an even more attractive weapon for the Kim regime. To deal with this threat, the U.S., ROK, and other allies will have to enhance their resiliency while devising strategies to deter, thwart, and neutralize the North Korean threat.
Cyber in the Context of North Korea’s Strategic Outlook
After the Korean War, North Korea developed asymmetric capabilities and tactics to exploit its enemies’ vulnerabilities and close the conventional capabilities gap.15 To that end, North Korea prioritized nuclear, chemical, and biological weapons of mass destruction (WMD) as well as the unorthodox use of artillery and other conventional capabilities. 16 South Korea’s Ministry of National Defense also concluded that the North would employ hybrid warfare, guerilla warfare, and blitzkrieg tactics. 17 In the event of conflict, Pyongyang’s objective would be to inflict a swift and devastating attack on the U.S. and/or South Korea to force a stalemate. 18
Cyber operations have become central components of North Korea’s asymmetric military strategy, peacetime provocations, and illicit activities. Kim Jong Un has reportedly said, “Cyber warfare, along with nuclear weapons and missiles, is an ‘all-purpose sword’ that guarantees our military’s capability to strike relentlessly.”19 Not only does cyber provide command and control advantages, but the flexibility of cyber weapons – especially compared to conventional and nuclear weapons – provides additional strategic options across the entire spectrum from peace (or armistice20) to war. In particular, the difficulty of attributing cyber attacks provides Pyongyang’s leadership with plausible deniability, thereby reducing the risk of retaliation and allowing it to operate in the gray zone between peace and war. 21
Kim Heung Kwang, a North Korean defector who taught computer science at Hamheung University, assessed that North Korea’s military heavily integrates information warfare into contemporary warfighting plans. 22 North Korea’s “quick war, quick end” strategy prioritizes compromising an enemy’s command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR) capabilities. CSIS’ Jenny Jun, Scott LaFoy, and Ethan Sohn note, “North Korean cyber doctrine, if one exists, may be premised on the idea that an extensively networked military is vulnerable to cyber capabilities.” 23
Experts believe that North Korea does not yet possess the capability to engage in sustained cyber warfare against military targets in a direct confrontation with the United States. Instead, they speculate that North Korean cyber attacks in a live-war scenario could target civilian entities whose paralysis would disrupt U.S. and South Korean military capabilities. For instance, Jason Healey of Columbia University suggests that North Korean cyber attacks in wartime would focus on American shipping and airports to disrupt the transport of additional forces to the region. Similarly, for South Korea, the North’s cyber forces could target transportation and financial infrastructure to increase public panic and delay evacuation of Seoul. Such operations would only require rudimentary disruptive capabilities, such as DDoS attacks and ransomware, which North Korean operators have used in the past. 24 In short, North Korea likely cannot win a cyber war, but it could hobble the U.S. and its allies using disruptive capabilities in a wartime scenario.
Cyber operations also play a crucial role in North Korea’s “peacetime provocations” strategy: North Korea incites unrest and disrupts the status quo without crossing the threshold of war to win political and economic concessions that ensure the survival of the Kim family regime. 25 Peacetime provocations force Pyongyang’s targets to choose between escalating tensions and acquiescing to North Korean demands. 26 Showcasing and testing nuclear weapons and ballistic missiles was the cornerstone of this strategy. 27 The North Korean government also relied on violence and state-sponsored crime, such as the assassination raids and attempted bombings of the 1960s. 28 Today, cyber-enabled economic warfare operations potentially provide a low-cost, alternative tool to diversify these peacetime provocations. The North could extort concessions by simply posing the threat of a CEEW attack on a target critical to its adversaries’ economic strength and vitality. If North Korea agrees to limit its nuclear weapons program, cyber-enabled economic warfare will likely become an even larger component of this peacetime provocation strategy. And unlike the North’s development of nuclear weapons, which did not stop the growth of South Korea’s economy from one of the poorest in the world in 1960 to one of the richest today, a purposeful campaign of CEEW could potentially curtail the greatest advantage the South holds over the North.
Another component of the strategy to ensure the survival of the Kim regime is the generation of hard currency. For decades, North Korea has used illicit financial activities to fund the regime’s military capabilities and the lavish lifestyle of the Kim family. These activities include narcotics production and distribution, trafficking of endangered species, counterfeiting currency, and manufacturing counterfeit cigarettes. 29 Cyber crime is another way the regime illicitly funds itself. The cyber heist targeting the Bank of Bangladesh stole $81 million. 30 If such heists were common, cyber crime could become Pyongyang’s primary source of illicit revenue.
This pursuit of revenue likely aligns with broader trends in North Korea’s malicious cyber activities. According to security experts at Cisco, “Revenue generation is still the top objective of most threat actors.” They warn, however, that “some adversaries now have the ability—and often now, it seems, the inclination—to lock systems and destroy data as part of their attack process,” calling this “new and devastating type of attack” a “Destruction of Service (DeOS).” 31 As North Korea continues to advance and fine-tune its destructive cyber tools and capabilities, Kim Jong Un may see an advantage in shifting from revenue generation to destructive cyber attacks against U.S. and allied targets, including critical infrastructure, industrial supply chains, and systemically important firms in key industries.
The limited scope of Pyongyang’s observed cyber attacks suggests that Kim Jong Un and his cyber operators may currently believe that destructive operations create more risks than benefits. However, if the regime were to experience a drastic crisis in relations with its adversaries, it may conclude that destructive cyber attacks would enhance deterrence and promote survival.
North Korean Cyber Personnel, Tools, Resources, and Internet Infrastructure
The South Korean Ministry of National Defense reported in 2014 that North Korea has approximately 6,000 cyber operatives who conduct “cyber warfare, including the interruption of military operations and attacks against major national infrastructure.” 32 For comparison, that is roughly the same number of troops in U.S. Cyber Command’s mission force. Though such comparisons are imprecise at best, the most important considerations are North Korea’s capabilities and intentions, which are difficult to assess. 33 Despite the common view that North Korea is so impoverished it has minimal technical capabilities, Pyongyang has devoted substantial time and resources to advancing its cyber power. Defector Kim Heung Kwang suggested the North Korean government allocates 10 to 20 percent of its military budget to cyber operations, a figure that has not been verified. 34 Ultimately, one can only speculate about the extent of North Korea’s cyber personnel and their funding. 35
Bureaucratic Structures
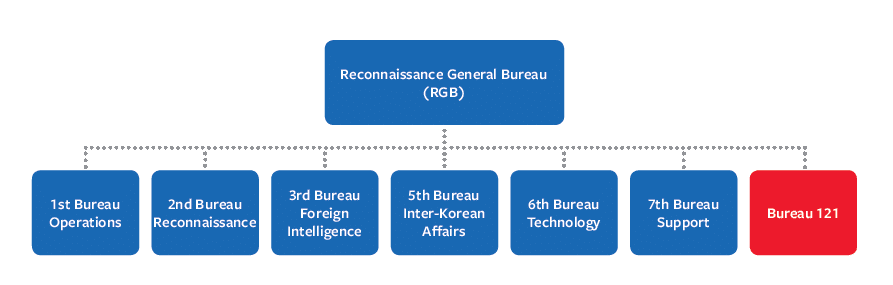
The Reconnaissance General Bureau (RGB) is the regime’s primary agency responsible for cyber activity. 36 Established between 2009 and 2010 amidst a restructuring of the country’s intelligence and national security organs, 37 the RGB is independent of the North Korean conventional military, the Korean People’s Army (KPA), and reports directly to the regime’s highest decision-making body, the State Affairs Commission led by Kim Jong Un. 38 According to the Pentagon, the State Affairs Commission tasks the RGB with North Korea’s terrorist, clandestine, and illicit activities. 39 The bureau’s autonomy from the regular military and its inclusion of cyber specializing in clandestine and terrorist activities suggests that North Korea sees cyber capabilities as extending beyond military assets.
The U.S. Treasury Department sanctioned the RGB twice for its activities, first in 2010 under Executive Order 1355140 for facilitating North Korean arms trading, money laundering, and other illicit activities, 41 as well as in 2015 under Executive Order 13687 for being an entity controlled by the North Korean government42 to hold the Kim family regime accountable for the Sony Pictures hack. 43 The United Nations also sanctioned the RGB following Pyongyang’s fourth nuclear test on January 6, 2016. 44
Reconnaissance General Bureau (RGB) 45
Bureau 121 is the primary RGB office for cyber duties. 46 Bureau 121 is instrumental in technical reconnaissance tasks as well as disruptive operations, such as infiltrating computer networks, hacking to extract foreign intelligence, and deploying viruses on adversary computer networks. 47 Additionally, the bureau allegedly tasked its hackers with attacking South Korean businesses. 48 The RGB created it “sometime after” 2013, according to threat intelligence firm Recorded Future. 49 The Korean Institute of National Unification (KINU), a South Korean government-funded think tank, assessed the bureau is made up of approximately 300 agents. 50 However, there are conflicting estimates. For instance, Jang Se Yul, a North Korean defector who studied computer science at North Korea’s University of Automation, stated there were 1,800 agents in Bureau 121. 51
Bureau 121 is based at the main RGB headquarters in the Moonshin-dong area of Pyongyang, according to the Center for Strategic and International Studies. 52 Until recently, Bureau 121 also operated a supplementary command post in the Chilbosan Hotel in Shenyang, the capital of Liaoning province in China. 53 In January, the Shenyang city government closed the hotel as part of Beijing’s increased compliance with UN sanctions. According to South Korean newspaper The Chosun Ilbo, a notice on the hotel front door stated, “We’ve closed down according to an administrative order from the Shenyang city government. All business operations of the hotel have stopped.” 54 It is unclear if the hackers operating out of the Chilbosan Hotel returned to North Korea or relocated to a third country. Previously, North Korean cyber attacks have originated from China, India, Malaysia, Vietnam, and New Zealand, to name a few. 55
Unit 180 is another hacking unit allegedly responsible for attacking financial institutions. According to North Korea defector Kim Heung Kwang, Unit 180’s cyber operations focus on stealing money from foreign banks. 56 Although he defected in 2004, Kim claims he still has contacts inside North Korea that provide him with current and relevant information. He notes that Unit 180 hackers generally operate overseas to make it harder to attribute their operations to North Korea. 57 Kim Heung Kwang did not specify whether this unit is independent of Bureau 121.
The North Korean military has also developed cyber capabilities separate from the RGB. Within the KPA, cyber programs are operated by the General Staff Department (GSD). The GSD is responsible for KPA’s preparedness for war. 58 Its primary responsibility regarding cyber is to integrate emerging tools and weapons into North Korea’s warfighting strategy. 59 The KPA does not have a single cyber command but rather divides information warfare, electronic warfare, psychological warfare, and related tasks between its Operations Bureau, Communications Bureau, Electronic Warfare Bureau, and Enemy Collapse Sabotage Bureau. 60 The GSD’s Command Automation Bureau is responsible for conducting cyber warfare operations. 61
The Lazarus Group
In 2016, the private cyber security company Novetta identified Lazarus Group in connection with the Sony Pictures attack. Novetta noted that the group “has been active since at least 2009, and potentially as early as 2007, and was responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment.” Novetta did not tie the Lazarus Group directly to the North Korean government, but noted that the Sony attack “was carried out by a single group, or potentially very closely linked groups, sharing technical resources, infrastructure, and even tasking.” 62 Previously, the FBI had attributed the Sony attack to the North Korean government, noting that a group calling itself “Guardians of Peace” had claimed responsibility. 63 The FBI based its assessment on technical similarities in the code, encryption algorithms, data deletion methods, and infrastructure used in prior North Korea-affiliated attacks. Subsequent investigations of the same malware samples by Kaspersky Labs, McAfee, and Recorded Future found traces of Lazarus malware tools and shared network infrastructure. 64
In 2017, the U.S. government determined that actors responsible for the “Hidden Cobra” campaign were also members of the Lazarus Group and the Guardians of Peace. Washington also linked the WannaCry attacks to this same group. 65 The U.S. government and private security firms have not specified, however, if Lazarus Group is affiliated with Bureau 121 or other offices in the North Korean bureaucracy.
Educational Institutions and Research Centers
North Korea recruits and trains its cyber operators through the regime’s education system. Within North Korea’s primary schools, students that excel in mathematics and science are separated from others to pursue special training, according to defectors. 66 This training includes computer-related classes, but also foreign language study, such as Chinese, Japanese, and English. 67 The regime reportedly then selects the top 500 students from secondary schools for training at the university level. 68 Selected students attend universities such as Kim Il Sung University College of Computer Science, Kim Chaek University of Technology, Mirim University, and several others. Students train to become state-sponsored hackers as well as software and hardware developers for indigenous North Korean technology companies. 69
Of the technology and cyber programs, Mirim University appears to be the most selective as it chooses only 100 students each year for its specialized five-year cyber intelligence and warfare program. The university’s curriculum includes command automation, programming, automated reconnaissance, and electronic warfare. 70 According to KINU, Mirim University serves as a direct conduit to the RGB, and the RGB accepts the top 10 graduates from the university each year. 71
Defectors have reported that among the 500 students selected annually for university-level training, some study abroad in China and Russia. 72 An anonymous North Korean defector, using the pseudonym Jong, reported that the regime selected him to study computer science at an early age based on his test scores. He went on to study abroad in China in his third year at university. After finishing his degree, Jong first worked for a state-owned software development agency and later in China as a state-sponsored hacker. According to Jong, the North Korean regime also sends newly trained hackers to China to earn money for the regime. Operatives study beta versions of video games and anti-virus software and create pirated versions to sell online through Chinese clients. 73
The state-run Korea Computer Center (KCC) is the regime’s premier IT research and development center. It also serves as the authority for production, management, distribution, and sale of its products. The KCC reportedly has nine production centers and 11 regional centers74 and operates overseas offices in Germany, China, and Syria. 75 KCC has developed products such as Samjiyeon tablet PCs and the Linux-based Red Star operating system. 76
KCC personnel have been involved in cyber crimes that directly benefitted the regime. In 2011, KCC employees operating in China collaborated with Chinese hackers to develop and sell software exploits for a popular South Korean online videogame called Lineage. 77 The South Korean government indicted five South Korean nationals who distributed this software exploit after purchasing it from North Korean developers based in Heilongjiang, China. The South Korean investigation connected the North Korean developers in China to KCC and determined they were earning revenue for Office 39, 78 which is the state entity in charge of amassing personal funds for the North Korean leader. The U.S. Treasury Department sanctioned Office 39 on August 30, 2010 for engaging in illicit economic activity to support the North Korean government. 79 In June 2017, Treasury also sanctioned KCC for generating funds to support the Kim family regime and the U.S.- and UN-sanctioned Munitions Industry Department, which oversees ballistic missile development. 80
Network and Internet Infrastructure
North Korea divides its domestic internet service between its nationwide Kwangmyong ‘intranet’ with no connection to the World Wide Web and a separate service that provides a limited outward facing internet connection. 81The Ministry of Posts and Telecommunications is responsible for distributing North Korea’s outward facing internet addresses through the Star Joint Venture Company. 82 Since 2010, Chinese internet provider Unicom has provided the first link that connects Star Joint Venture Company to the World Wide Web. 83 Intermittent electric power outages further limit the capacity of North Korea’s internet and intranet networks.84
The regime reserves its outward facing connection for elites as well as students training to become Pyongyang’s cyber warriors. It heavily monitors users for any subversive activity. 85 Following an extended U.S. Cyber Command campaign to cut off North Korean internet access, 86 North Korea opened a new outward facing internet connection in October 2017 provided by the Russian telecommunications company, TransTelecom. 87 The addition of this Russian network could strengthen Pyongyang’s resilience against U.S. cyber actions. 88
Given the regime’s total control over the nation’s internet activity, Hewlett-Packard’s security experts conclude that North Korea’s cyber operators “do not typically launch attacks directly from within North Korea.” Attribution would be too easy. 89 Defectors have corroborated that the North Korean government sends its hackers abroad so that Pyongyang can obfuscate their origin. 90 Indeed, Recorded Future detected a “near absence” of malicious cyber activity originating from inside North Korea between April and July of 2017, a time of increased hostility between North Korea and the United States. 91
North Korea reportedly has a significant physical and virtual presence in China, India, Malaysia, New Zealand, Nepal, Kenya, Mozambique, and Indonesia for launching malicious cyber operations. According to Recorded Future, 10 percent of all malicious North Korean cyber activity emanates from China, and another 20 percent from India. 92 Defectors have verified that North Korea deploys teams of hackers to carry out offensive cyber operations in Shenyang, China. 93 Recorded Future suggest there could be North Korean operatives, most likely students, operating from at least seven Indian universities and as research institutes. 94
North Korea’s IT Industry
In 2015, the Center for Strategic and International Studies assessed that North Korea prioritized the development of an indigenous information technology (IT) industry for software development. 95 The Ministry of Electric Power Industry and the Ministry of Posts and Telecommunications oversee North Korea’s IT industry. 96
North Korean firms now provide a wide range of products and services including “website and app development, administrative and business management software, radio and mobile communications platforms, IT security software, and biometric identification software for law enforcement,” with customers across China, Russia, South Asia, the Middle East, and Africa. 97
A notable company involved in North Korean IT exports is Malaysia-based Glocom, which the UN Panel of Experts identified as a front for the RGB. 98 While Glocom is a defense firm that sells radios, military communications equipment, battle management systems, and command-and-control systems, 99 North Korean individuals affiliated with Glocom, such as Kim Chang Hyok, operate IT companies, such as Malaysia-based WCW Resources Sdn Bhd. 100 Kim Chang Hyok is the representative of a Singapore-based company called Pan Systems. Pan Systems allegedly operates Glocom, according to Reuters. 101 Analysts at the James Martin Center for Nonproliferation Studies of the Middlebury Institute of International Studies warn that North Korea could use indigenously developed software to disseminate malicious code, although no such reported incidents have yet occurred. 102 The revenue generated by these IT companies does, however, provides an alternative source of income for the Kim family regime and also undermines UN sanctions.
North Korean Cyber Tactics and Capabilities: Case Studies and Lessons Learned
North Korea first demonstrated its emerging cyber capabilities in July 2009 when its operators carried out a series of DDoS attacks on 27 different South Korean and American websites belonging to government agencies, banks, and major corporations. The goal was to slow down and disrupt web services in both the U.S. and South Korea. 103 North Korea’s cyber capabilities have improved significantly since then, with Pyongyang attacking a diversified range of targets, using various methods. The case studies below cover the range of North Korea’s evolving cyber capabilities. While the majority of North Korea’s current cyber activity is focused on making – or stealing – money or collecting data for the regime, the technical capabilities that the regime is perfecting could be leveraged in cyber-enabled economic warfare operations.
Since 2011, North Korea’s cyber capabilities have moved beyond DDoS attacks. With each subsequent operation, North Korea has demonstrated new ways its hackers can use cyber-enabled tools to not only disrupt and destroy, but also to steal money, steal data, and impose terror on its victims. Increasingly, North Korea has used cyber operations to steal data and engage in intelligence operations. For instance, in 2016, North Korea stole 235 gigabytes of data containing classified wartime contingency plans for the U.S. and South Korean forces. 104
The South Korean government suffers an estimated 1.5 million cyber intrusions every day. 105 South Korean police authorities reported between 2014 and 2016 that North Korean cyber operators successfully infiltrated more than 140,000 computers across 160 South Korean private firms and government agencies in order to plant malicious code that is “laying the groundwork for a massive cyber-attack.” 106
These North Korean cyber operations hold dangerous implications for CEEW. As the world conducts its financial and commercial activity through computer-based software and systems, bad actors can exploit this technology. North Korea’s hackers could use cyber-enabled means to disrupt or cause lasting damage to the online financial infrastructure that helps modern economies function. Targeting the South Korean, or even American, economy fits into Pyongyang’s asymmetric security strategy.
Although it is important to consider the potential threat of CEEW attacks, one cannot be certain the Kim regime has the intent to do so. Pyongyang’s primary strategic objective is prolonging the Kim regime’s survival, according to the U.S. Department of Defense. 107 Pyongyang thus calibrates its offensive cyber activity to remain in the “gray zone,” which U.S. Special Operations Command defines as a realm of “competitive interactions among and within state and non-state actors that fall between the traditional war and peace duality.” 108 “Gray zone” operations are also often asymmetric attacks enemy “in venues in which it cannot easily respond in kind,” according to Richard Andres of the National Defense University. 109 In response to North Korea’s current cyber theft, espionage, and reconnaissance operations, the U.S. and other victim nations often have few options for proportionate retaliation, resulting in a difficult choice between appeasement and escalation.
North Korea may avoid conducting sustained CEEW operations because of its desire to remain within the gray zone. However, this could change with North Korea’s perception of its security environment. Tensions have receded for the moment as the result of the Trump-Kim summit and subsequent return to negotiations, yet analyst Victor Cha assesses that a breakdown in the diplomatic process could bring the U.S. and North Korea closer to war since it would leave “no other recourse for diplomacy.” 110 The following case studies highlight the North’s capabilities and how it could leverage them if tensions rise.
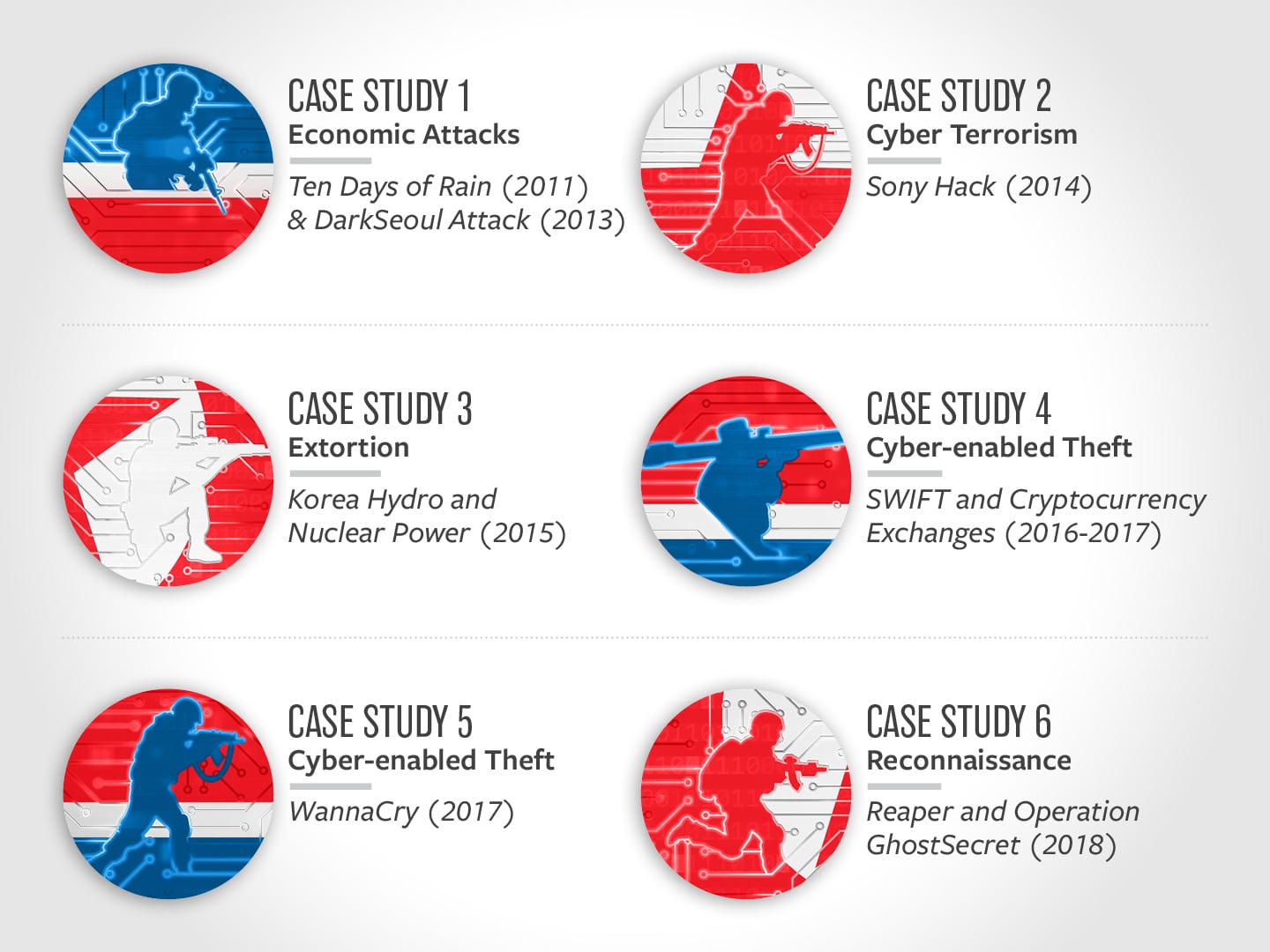
Case Study 1: Economic Attacks – Ten Days of Rain (2011) and DarkSeoul Attack (2013)
In March 2013, North Korean state-sponsored hackers unleashed a major cyber attack, known as DarkSeoul, against three major South Korean banks and three media companies. Hackers used malware to damage thousands of computers and disrupt critical servers. 111 The virus deployed a complex type of wiper malware that irreversibly deleted and wrote over the compromised target’s master boot record, considered the “most important data structure” of the computer, 112 rendering the affected computers useless.
The DarkSeoul attacks marked a new phase in North Korea’s cyber operations. Not only did the malware’s destructive power inflict financial costs estimated at $800 million, 113 it caused major delays and confusion for 10 days in South Korea’s financial system. 114 The attack also shut down the three target banks’ operations for days. 115 A South Korean task force of military, government, and civilian experts analyzed the codes and supporting network infrastructures to conclude that North Korean government-backed hackers perpetrated the attack. 116
The DarkSeoul attack is the clearest example of a potential North Korean cyber-enabled economic warfare operation. The 2013 attack not only imposed significant costs to restore banks and media companies’ lost computer hardware, but also temporarily undercut South Korea’s banking and financial infrastructure. DarkSeoul, however, was not the first time North Korea used cyber-enabled means to disrupt South Korea’s banking sector. In 2011, the Ten Days of Rain DDoS campaign took down Nonghyup Bank’s nationwide branches, automated devices, and online banking services for 10 days. 117 This incident, however, was part of a broader disruption campaign that not only targeted Nonghyup Bank, but also South Korea’s government, military, and private industry. 118
Both the DarkSeoul cyber attack and earlier 2011 incident was to test the regime’s capabilities and tools to someday undermine Seoul’s national power. The North Korean cyber operatives’ ability to disrupt the South’s financial sector suggests Pyongyang could do it again in the future, and perhaps at a larger scale as capabilities improve.
Case Study 2: Cyber Terrorism – Sony Hack (2014)
On November 24, 2014, a hacker group calling themselves the Guardians of Peace broke into the computer systems of Sony Pictures and threatened to release company data if Sony did not cancel the release of an upcoming film, “The Interview,” a comedy depicting a farcical plot to assassinate Kim Jong Un. The hackers also threatened 9/11-style terror attacks on theaters that screened the film. 119 Although Sony Pictures canceled the film’s theatrical release, the hackers still released the data and used malware to destroy approximately 70 percent of Sony Pictures’ computers. 120
The wiper malware and phishing campaigns in this operation had similar characteristics to the ones the DarkSeoul hackers employed. In the Sony attack, hackers gained access through both phishing emails and software vulnerabilities on the company’s website to access backend databases housing IT blueprints and employee private information. 121 Hackers then used wiper malware called Destover to erase the data.
The FBI attributed the attacks to Pyongyang. Technical analysis revealed links to other malware attributed to the North Korean government. North Korean-related IP addresses were in communication with the IP addresses hard coded into the data deletion malware, thereby revealing a significant overlap in the cyber infrastructure between the Sony attack and other malicious activity linked to the North Korean government. The attack also shared structural and tactical similarities with the DarkSeoul attacks. 122
The stated objective of the Sony hackers was to prevent the release of the disputed film because it harmed Kim Jong Un’s public image. 123 Only a month earlier, in October 2014, North Korean cyber operatives targeted British film production firm Mammoth Screen, which was set to produce a new television drama involving a British nuclear scientist taken hostage in North Korea. North Korea cyber operatives infiltrated Mammoth Screen but did not deploy destructive malware. Despite this, BBC reporting suggested that “the presence of North Korean hackers on the system caused widespread alarm over what they might do.” This prompted the firm to delay the release of the series, which it eventually scrapped due to complications in funding. 124 In both cases, Pyongyang targeted a noncombatant and nongovernment entity and used threats to compel them to take specific actions. The Washington Post reported that anonymous analysts assessed that the Sony Pictures attack set a “worrying new precedent for cyberterrorism.” 125 The reason analysts classified the Sony hack as cyber terror was because the attackers threatened both the company employees and theatergoers. 126 The political intent of the coercive action, i.e. protecting the perceived legitimacy of Kim Jong Un, is also consistent with terrorism.
Were North Korea to unleash a similar attack on U.S. or South Korean infrastructure, there would be significant national security implications. North Korea has already used spear-phishing campaigns against U.S. electric power companies as part of “early-stage reconnaissance,” according to experts at FireEye, 127 and in November 2017, the U.S. Department of Homeland Security and FBI issued a joint technical alert warning that North Korean cyber actors were targeting aerospace, telecommunications, and finance industries. 128 Some of the malware North Korea used in the Sony attack provided backdoor access to compromised systems, while other malware served as a remote access tool that could execute multiple commands the hacker can issue from a central command-and-control server. 129 These capabilities would likely play a key role in any attack on critical infrastructure.
Case Study 3: Extortion – Korea Hydro and Nuclear Power (2015)
In 2015, the South Korean government revealed that civil nuclear company Korea Hydro and Nuclear Power (KHNP) had suffered a cyber attack the prior December. This attack bore the traits of a North Korean operation, specifically the Sony Pictures hack. It is unclear why the South Korean government did not formally attribute the attack to anyone. 130 Cyber operatives infiltrated the company’s networks through spear-phishing emails that targeted 3,571 employees. The hackers then released the personal information of 10,799 employees. 131 The hackers also posted a ransom notice on Twitter claiming they stole proprietary information regarding South Korea’s nuclear reactors and then posted the stolen documents online. 132 The hackers threatened to sell this information to “many countries from Northern Europe, Southeast Asia, and South America.” 133 Finally, the hackers threatened to cause physical destruction to the KHNP facilities unless the company shut down three of its 23 nuclear reactors. It is unclear what the hackers’ motives were for demanding the shutdown, but they presented themselves as anti-nuclear activists. Demanding the shutdown reinforced the credibility of their self-presentation as activists and prevented the ROK from attributing the attack to the North Korean government. 134
Given the conflicting demands for ransom payments and a reactor shutdown, it is unclear whether the goal was merely to extort money or to pursue CEEW. In their ransom note, the hackers warned that South Korea’s government risked undermining its efforts to export nuclear reactors if it did not meet their demands. This incident revealed South Korea’s civil nuclear plants and energy sector are vulnerable to cyber attacks. Furthermore, undermining a key economic sector of the South Korean economy would not only weaken the economic output of the nation, but also threaten broader national interests.
Case Study 4: Cyber-enabled Theft – SWIFT and Cryptocurrency Exchanges (2016-2017)
Cyber security firms have attributed 18 separate cyber attacks in countries such as Costa Rica, Ethiopia, Gabon, India, Indonesia, Iraq, Kenya, Malaysia, Nigeria, Poland, and several others to the North Korean hackers known as the Lazarus Group. The most notable attack occurred on February 4, 2016, when the group stole $81 million from Bangladesh’s central bank. The hackers infiltrated the bank’s network, stole its credentials for the Society for Worldwide Interbank Financial Telecommunication (SWIFT), a financial messaging service, and issued requests through the Federal Reserve of New York to transfer funds from the Bangladeshi bank to accounts the hackers controlled. 135 In October 2017, BAE Systems reported a similar attack on Taiwan’s Far Eastern International Bank after hackers gained access to the bank’s SWIFT credentials. 136 BAE Systems’ report suggested this attack was part of a wider campaign that also included a Vietnamese commercial bank. BAE noted the malware in its system had similarities to the malware characteristics used in the Sony Pictures hack.
The SWIFT global message platform connects more than 11,000 banking, finance, and corporate customers. Any disruption to this service could yield severe economic and political effects. 137 Although the Kim family regime appears to prioritize currency generation in its objectives, these attacks using the SWIFT system raise concerns that North Korean hackers may become more proficient at manipulating the data and systems that undergird the global financial system. While a large enough attack on a major bank might have global repercussions, attacks on the SWIFT network would shake the core of the system.
The explosion of the cryptocurrency market is also providing a new attack vector. Cyber security firms report that North Korea’s cryptocurrency-generating operations include both hacking exchanges and mining currencies. 138 In September 2017, FireEye linked North Korea to a series of attacks on three ROK cryptocurrency exchange firms between April and July 2017. North Korean hackers used spear-phishing emails and their malware was similar to a virus used in prior North Korean cyber attacks on global banks in 2016. 139 In December 2017, North Korean hackers attacked the Youbit currency exchange and stole 17 percent of the exchange’s total digital assets, which had a value of 7.6 billion Korean won or $7 million. 140 As a result of the attack, Youbit declared bankruptcy.
North Korea has reportedly generated up to 11,000 bitcoins, or $120 million, from its attacks on cryptocurrency exchanges and currency mining. 141 This could have significant residual effects on South Korea’s financial infrastructure. In December 2017, South Korea was ranked the world’s third largest market for Bitcoin trading after Japan and the United States. Major South Korean corporations, including Nexon and Samsung, are reportedly investing in virtual currency businesses and supporting technologies. 142 As these businesses become more intertwined with South Korea’s formal financial system, attacks on cryptocurrencies could target the stability of Seoul’s banking system.
Case Study 5: Cyber-enabled Theft – WannaCry (2017)
Between February and May 2017, the WannaCry ransomware wreaked havoc worldwide. WannaCry infected more than 230,000 computers, including the National Health Service in the United Kingdom. Once this virus compromised a computer, it would find and encrypt 176 different file types, demanding a $300 payment in bitcoin to decrypt the locked files. 143 Prior to May, the effects were more limited because the virus relied on “stolen credentials to move through infected networks, while the May 12 version included the ability to self-propagate,” according to experts at cyber security firm Symantec. 144 The final iteration of the virus was able to propagate itself across thousands of computers by leveraging a software vulnerability, known as the Eternal Blue exploit, allegedly stolen from the U.S. National Security Agency and publicly revealed in April 2017 by a Russian-linked hacker group called Shadow Brokers. 145
Shadow Brokers released the Eternal Blue vulnerability into cyber space for use by any hacker, but the fact that North Korea quickly incorporated the exploit into its active operations suggests that North Korea is active on the malware black market. Although there is no documentation of North Korea facilitating cooperation between state-sponsored and private hackers, Pyongyang’s track record of cooperation with organized crime146 and rogue states raises concerns that North Koreans could expand these efforts in cyber space. 147
The North Korean government emerged as a likely suspect when Symantec found remnants of code linked to the Lazarus Group on computers infected with WannaCry, including malware used in the Sony hack. 148 In December 2017, the U.S. government publicly attributed the WannaCry attack to North Korean state-sponsored actors. 149
Ultimately, even as the virus infected computers in more than 150 countries, 150 the hackers generated little income because a flaw in the code prevented them from collecting bitcoin payments. 151 Still, the attack cost the affected companies billions of dollars. 152 And as costly as the attack was, it could have been far worse if North Korea had paired the worm with wiper viruses, instead of malware, and aimed directly at U.S. and allied critical infrastructure. Microsoft also minimized the damaged when it issued a patch to address the Eternal Blue vulnerability two months prior to the attack. 153
Case Study 6: Reconnaissance – Reaper and Operation GhostSecret (2018)
In February 2018, FireEye revealed the existence of an extended reconnaissance operation dubbed Advanced Persistent Threat 37, or Reaper, which engaged in covert intelligence gathering in support of a range of North Korean state interests. 154 In April 2018, McAfee exposed a North Korean global data reconnaissance operation targeting a broad range of industries in critical infrastructure, entertainment, finance, health care, and telecommunications. This extended campaign, dubbed Operation GhostSecret, began in mid-February 2018. The operation deployed several malware implants derived from prior North Korean attacks. 155 According to McAfee, the operation stole data from affected systems, and the attackers designed their code to evade detection and “deceive forensic investigators.” 156
The operation reportedly began with a campaign known as Bankshot against the Turkish financial system, which bore similarities to North Korea’s attacks on SWIFT. 157 Within two weeks, the operation had compromised telecommunications, health, finance, critical infrastructure, and entertainment companies across 17 different countries. 158
GhostSecret was notable because of the extensive command structure that supported the malware implants. McAfee called the infrastructure “an extensive framework for data reconnaissance and exfiltration.” The command and control infrastructure not only supported the data exfiltration but also had arbitrary command execution capabilities on a victim’s system. 159
North Korea’s ongoing cyber reconnaissance operations, such as APT 37 Reaper and Operation GhostSecret, enable hackers to pre-position exploits and gain insights into the battlefield and into the vulnerabilities of the U.S. and its allies. These operations also enable the Kim family regime to develop contingency plans for direct conflict with its adversaries. Indeed, North Korea may now be scouting the battlefield in case diplomatic efforts reach the end of the road.
Policy Recommendations
China and Russia have conducted (and are conducting on an ongoing basis) a range of cyber operations against the United States – from information operations to cyber-enabled economic warfare. North Korea is no doubt taking notes. The North Korean regime is a “learning organization.” It observes best practices and incorporates them into its arsenal. 160 Therefore, Washington’s responses to combat, counter, thwart, and deter other malicious cyber actors will likely have an impact on North Korea’s capabilities and strategies. For that reason, policymakers must adopt optimal cyber defense measures in addition to heeding recommendations specific to the threat from North Korea.
Enhancing U.S. cyber resilience and working cooperatively with the private sector are central to any effective cyber defense strategy. For example, the U.S. Computer Emergency and Readiness Team (US-CERT) issues technical alerts that inform critical infrastructure, financial, and aerospace companies how to address software vulnerabilities.161 Ensuring that American businesses incorporate US-CERT technical recommendations may be one way to turn information sharing into effective resilience.
U.S. Computer Emergency Readiness Team (U.S.-CERT) Alerts and Reports on North Korea Malware162
| Type and Title | Date | Objective |
| Alert (TA17-132A) Indicators Associated with WannaCry Ransomware |
May 12, 2017 | Provided a comprehensive overview of the vulnerabilities that WannaCry Ransomware exploits and recommended steps for prevention/protection |
| Alert (TA17-164A) HIDDEN COBRA: North Korea’s DDoS Botnet Infrastructure |
June 13, 2017 | Provided technical details on the infrastructure and cyber tools for North Korean government-sponsored hackers targeting media, aerospace, financial, and critical infrastructure sectors in U.S. and abroad |
| Malware Analysis Report (MAR-10132963) Analysis of Delta Charlie Attack Malware |
August 23, 2017 | Provided file samples of the Delta Charlie Attack Malware to create defense systems for vulnerable devices and networks |
| Alert (TA17-318B) HIDDEN COBRA– North Korean Trojan: VOLGMER |
November 14, 2017 | Provided information regarding capabilities, infrastructure, and response methods to the Volgmer malware that targets the government, financial, automotive, and media industries |
| Alert (TA17-318A) Hidden Cobra North Korean Trojan: FALLCHILL |
November 14, 2017 | Provided information regarding capabilities, infrastructure, and response methods to the Fallchill malware that targets the aerospace, telecommunications and financial industries |
| Malware Analysis Report (MAR-10135536) North Korean Trojan: BANKSHOT |
December 21, 2017 | Provided analysis and samples of seven malicious executable files related to the Bankshot malware |
| Malware Analysis Report (MAR-10135536-G) North Korean Trojan: BADCALL |
February 13, 2018 | Provided analysis and samples of three malicious files related to the Badcall malware |
| Malware Analysis Report (MAR-10135536-F) North Korean Trojan: HARDRAIN |
February 13, 2018 | Provided analysis and samples of three malicious files related to the Hardrain malware |
| Malware Analysis Report (MAR-10135536.11) North Korean Trojan: SHARPKNOT |
March 28, 2018 | Provided analysis and a sample of a 32-bit Windows executable file related to the Sharpknot malware |
| Malware Analysis Report (MAR-10135536-3) HIDDEN COBRA RAT/Worm |
May 29, 2018 | Provided analysis of four unique files, including an installer and additional malware that served as a Remote Access Trojan (RAT) and a malicious Dynamic Link Library (DLL) that served as a Server Message Block (SMB) worm that was on behalf of the North Korean government |
| Alert (TA18-149A) Hidden Cobra Joanap Backdoor Trojan and Brambul Server Message Block Worm |
May 29, 2018 | Shared information on the IP addresses and indicators of compromise (IOCs) associated with the Joanap Remote Access Trojan (RAT) and a Server Message Block (SMB) worm Brambul, both of which targeted the media, aerospace, financial, and critical infrastructure sectors |
| Malware Analysis Report (10135536-12) North Korean Trojan: TYPE FRAME |
June 14, 2018 | Provided analysis and samples of 11 malware related to the TYPEFRAME malware |
| Malware Analysis Report (10135536-17) North Korean Trojan: KEYMARBLE |
August 9, 2018 | Provided analysis and a sample of the Remote Access Trojan malware variant named Keymarble in the form of a 32-bit Windows executable file |
Additionally, the U.S. military must be able to continue operating during cyber attacks. The development and public demonstration of resilient capabilities may reduce the adversary’s likelihood of conducting an attack if it knows the chances of success are lower. For example, capabilities already exist to protect the operations of financial markets during anomalies in market activity, as well as in a crisis. Future cyber attacks will no doubt test these capabilities.
Further, the United States needs to enhance societal resilience in the face of cyber attacks. The U.S. government should therefore explore education and training programs similar to the Cold War civil defense programs that entailed preparing for a nuclear attack. A 21st century cyber civil defense program would mitigate and reduce the risks of cyber attacks against critical infrastructure. For example, what should Americans do if they lose access to their bank accounts in a widespread cyber attack? A civil defense program could minimize public panic and potentially speed recovery.
In addition to such general measures, the U.S. government should consider the following recommendations aimed at addressing the specific cyber threats from North Korea.
1. Create a combined ROK-U.S. Cyber Task Force
Since the ROK and U.S. are the primary targets for North Korean cyber activities, the alliance should establish a task force of ROK and U.S. cyber experts to synchronize defenses and options for offensive operations. Although joint task forces are often ineffective, a combined entity should be pursued to ensure the alliance could adequately defend against the full range of North Korea’s cyber threats, from CEEW to wartime cyber operations.
On June 21, the 5th U.S.-Republic of Korea Bilateral Cyber Consultations were held in Seoul “to discuss a wide range of cyber issues, including cooperation on deterring cyber adversaries, cybersecurity of critical infrastructure, capacity building, information sharing, military-to-military cyber cooperation, cybercrime, international security issues in cyberspace, and current threats and trends in the international cyber environment.” 163 An agenda item for the next consultative meeting and for the ROK/U.S. security consultative meeting in fall 2018 should be the establishment of a permanent combined ROK/U.S. cyber task force to supplement periodic consultation. A permanent task force is necessary to defend economic infrastructure and address the full range of cyber threats, including CEEW.
The Cyber Task Force should develop a combined strategy for operations during both armistice and wartime. It should consist of military and civilian experts from across the U.S. and ROK governments and include private sector experts as well. This would not contradict the indefinite suspension of combined military exercises following the Singapore summit. In fact, given that North Korea is likely to continue or escalate aggressive cyber operations during nuclear negotiations, the task force’s mission is only more urgent.
The new task force should include enhanced information sharing. For instance, South Korea’s Korea Internet Safety Agency successfully prevented a spear-phishing campaign targeting 10 cryptocurrency exchanges earlier in 2017. 164 Sharing insights from such experiences will be instrumental in fortifying cyber defenses.
The United States National Cyber Strategy calls for developing international partner capacity to support a new cyber deterrence initiative. A Combined ROK-U.S. Task Force would be one example of operationalizing the strategy. 165
2. Disable the Reconnaissance General Bureau (RGB)’s network of front companies
Sanctions have been an underutilized tool to respond to North Korea’s cyber operations. Section 209 of the North Korea Sanctions and Policy Enhancement Act (NKSPEA) requires the president to sanction individuals and companies affiliated with North Korea’s malicious cyber activity. 166 In September 2018, the Treasury and Justice Departments took a major step forward by sanctioning and pressing charges against a North Korean computer programmer, Park Jin Hyok, who had a role in the Sony Pictures hack, the SWIFT Bangladesh Bank theft operation, and WannaCry. 167 Prior to this, the Treasury Department had acted only once. That was in January 2015 when Treasury sanctioned the RGB, two North Korean companies, and 10 North Korean government officials under Executive Order 13687 in response to the Sony Pictures cyber attack.
The U.S. government could do more to build on this momentum and impose the necessary financial pressure to curb North Korean cyber operations. 168 The RGB and its funding sources for its cyber operations remain largely untouched. The RGB continues to operate front companies around the world. 169 For example, the RGB-affiliated Glocom sells battlefield radio equipment in Malaysia in breach of UN sanctions. The company operates from within the Pyongyang branch of Pan Systems, a Singaporean company. 170 The United Nations Panel of Experts determined that the company is engaged in “patterns of evasion” using multiple overseas accounts and trusted local partners to move funds as part of North Korea’s illicit trade in “prohibited military communications technology.” 171The report identified the third parties and intermediaries that Glocom used as part of its schemes. The March 2018 report recommended the Security Council sanction the companies and individuals participating in Glocom’s illicit activities, including Pan Systems, International Global System, and International Golden Service.172
While Glocom is not directly involved in North Korea’s malicious cyber activities, it generates support for the RGB, as well as the full range of Pyongyang’s malign conduct. Sanctioning Glocom could therefore sever one of the RGB’s financial lifelines. The U.S. government should investigate all companies named in the UN Panel of Expert report with the goal of adding all of these entities to U.S. sanctions lists, pending confirmation of the report’s allegations.
Additionally, Washington should be more proactive in its engagement with foreign governments that host companies such as Glocom, Pan Systems, International Global System, and International Golden Service. If governments fail to investigate and act against RGB front companies, Washington should consider punitive measures such as secondary sanctions.
3. Pursue preparations for offensive measures to restrict Pyongyang’s cyber capacity
The U.S. and its allies must develop options to conduct offensive cyber measures to overwhelm and disrupt North Korea’s network infrastructure. Although classified plans are likely under development within specific government organizations, the use of offensive cyber capabilities remains a topic of debate and controversy. Given the threat posed by North Korea and the damage it can do to the U.S. and its allies, serious consideration must be given to offensive use of cyber capabilities to deter and defeat North Korean cyber operations. While pre-emptive use of offensive capabilities may be a dangerous provocation, such capabilities cannot be created after a cyber attack occurs and an immediate response is required.
4. Pressure foreign countries to dismantle North Korean networks in their jurisdictions
That the majority of North Korea’s cyber attacks originate outside the country constitutes a significant operational weakness. 173 The U.S. and its allies should increase diplomatic engagement with foreign nations to monitor and restrict the activities of North Korean personnel on their soil or to expel those that are involved in malicious cyber activities. The U.S. should also encourage these nations to stop suspected North Korean operatives from attending certain universities or working in specific research institutes which might provide the training North Korea’s hackers need.
If the foreign governments do not take steps to address malicious North Korean cyber operations emanating from their jurisdiction, the U.S. should be prepared to impose sanctions and other penalties on North Korea’s cyber enablers to show that complicity has consequences. 174 Section 209 of the North Korea Sanctions Policy and Enhancement Act (NKSPEA) requires the president to submit a comprehensive report that not only describes the North Korean cyber security threat, but also “the identity and nationality of persons that have knowingly engaged in, directed, or provided material support to conduct significant activities undermining cybersecurity.” Additionally, the legislation requires this presidential report to Congress to include a U.S. strategy that addresses how to “engage foreign governments to halt the capability of the Government of North Korea and persons acting for or on behalf of that Government.” 175
Both the executive and legislative branches should work together to ensure the White House issues this report every 180 days. This would not only fulfill NKSPEA’s requirements, but also ensure the gathering of crucial information that could put pressure on foreign governments that are enabling North Korean cyber activity. While NKSPEA authorizes the president to impose unilateral sanctions on those individuals and entities highlighted in the 180-day report, Washington should first warn these individuals and/or governments to cease and desist. If the cyber activity continues, Washington should then resort to imposing punitive sanctions.
Currently, China is the only country that has verifiably hosted North Korean hacker teams and supported network infrastructure. The Department of Justice revealed that North Korean cyber operatives, such as the charged and sanctioned programmer Park Jin Hyok, operated from China. 176 Although Beijing could deny any direct involvement in North Korea’s offensive cyber operations, China’s tacit consent enabling the presence of North Korean cyber operatives warrants action.
Beyond China, analysis of data transfers coming from nations such as India, New Zealand, Malaysia, Thailand, and others suggest a North Korean presence. However, it is difficult to confirm whether these nations knowingly host North Korean hacker teams. In any case, the U.S. should prioritize intelligence efforts and joint investigations with the countries in question.
Finally, the Consolidated Appropriations Act of 2018 contained a provision prohibiting U.S. aid to any country supporting North Korean cyber attacks. 177 This is a measures that could cause host nations to dismantle the North Korean networks within their borders. Washington must remind these host nations, particularly China, that there is a price to pay for overlooking the presence of North Korean cyber operatives.
5. Include cyber as part of North-South negotiations and North Korea-U.S. security discussions
When negotiating with North Korea, the U.S. must seek a comprehensive deal that addresses more than just its nuclear program. An agreement dedicated to curbing solely North Korea’s nuclear capabilities will leave key issues unaddressed. This includes human rights atrocities, WMD, conventional military capabilities, and cyber aggression. 178
Neither the April 27 Panmunjom Declaration nor the joint statement following the June 12 Singapore summit explicitly addressed cyber. Some will argue against including cyber activities on the same grounds that they argue against addressing human rights, namely that it would be a distraction from the nuclear negotiations. Yet the U.S. has avoided human rights discussions in nuclear negotiations for some 25 years without securing an effective nuclear agreement or improvements to North Korean human rights.
The failure to address North Korean cyber activities allows the regime to believe these are permissible provocations. All future security discussions and negotiations must include a cyber component, and the regime must know the consequences for employment of hostile cyber activities to include cyber-enabled economic warfare.
6. Incentivize publication of information about cryptocurrency hacks
Cryptocurrency exchanges have become a target of choice for cyber criminals. While North Korea has been blamed for some of the attacks, others remain unattributed or are the work of other cyber criminals. Because exchanges often do not publicize details about these hacks, it is difficult for outside researchers to analyze transactions and uncover the methodologies used in each attack.
No matter the level of threat, the United States and South Korea should issue breach notification rules and work with relevant authorities in other jurisdictions to require exchanges to release specific information about attackers, including the wallets where they deposit stolen funds. While taking steps to ensure the protection of clients’ identity, publicizing attack information would warn third parties against engaging in transactions with those wallets, and it would enable researchers to uncover illicit networks and patterns of transactions. Researchers could determine any connections between cryptocurrency hackers and those involved in ransomware or other malicious cyber exploitations. This greater visibility would enable law enforcement to better prosecute crimes and decision makers to better develop policies to combat these attacks.
Conclusion
Cyber is just one weapon in North Korea’s arsenal, yet it has given new leverage to Pyongyang. In particular, North Korea has demonstrated its capability and intention to target the economic livelihood of its adversaries through cyber-enabled means.
While North Korea has yet to unleash a large-scale crippling attack on Washington or Seoul, its persistent offensive cyber campaigns demonstrate that Pyongyang’s cyber capabilities improve day by day. North Korea has shown it can penetrate network defenses and even destroy compromised computers. And while North Korea’s cyber army is still a long way from posing an existential threat to the U.S. and its allies, treating cyber as an afterthought could be something Washington and Seoul may later regret.