January 31, 2019 |
Midterm Assessment: Cyber
Contents
January 31, 2019
Midterm Assessment: Cyber
Current Policy
The Trump administration’s cyber policy is moving away from the prioritization of law enforcement to an approach that balances law enforcement, persistent engagement with adversaries in cyberspace, and the pursuit of deterrence. The most significant expression of this shift is the administration’s September 2018 National Cyber Strategy, according to which the U.S. government will “Identify, counter, disrupt, degrade, and deter behavior in cyberspace that is destabilizing and contrary to national interests, while preserving United States overmatch in and through cyberspace.”1
The Trump administration inherited a cyber policy based on Presidential Policy Directive 20 (PPD-20) of January 2013. An unclassified White House summary of the directive explained, “It is our policy that we shall undertake the least action necessary to mitigate threats and that we will prioritize network defense and law enforcement as preferred courses of action” (emphasis added).2
During President Trump’s tenure, senior U.S. officials have issued blunt assessments of the previous administration’s approach. General Joseph Votel, commander of U.S. Central Command, noted that at the operational level, the approval process can be “so cumbersome that these capabilities are narrowly irrelevant.”3 Similarly, Admiral Mike Rogers, then serving as National Security Agency director and commander of U.S. Cyber Command (CYBERCOM), testified before Congress in February 2018 that U.S. cyber capabilities were “not optimized for speed and agility.” Moreover, he stated, U.S. adversaries are “more emboldened” because they do not believe they will suffer significant consequences for their actions.4 Incoming National Security Agency and CYBERCOM head General Paul Nakasone similarly testified a few days later, “We need to impose costs on our adversaries to ensure mission success by persistent delivery of cyberspace effects.”5
The Trump administration appears to have taken these critiques and recommendations to heart. In May 2017, the president signed an executive order requiring departments to work with the private sector to support critical infrastructure security. Seven months later, in its first National Security Strategy, the administration pledged to impose “swift and costly consequences” on malicious cyber actors, and explicitly noted the danger of adversarial cyber-enabled economic warfare.6
Meanwhile, the Department of Defense’s September 2018 Defense Cyber Strategy stated the department will “deter malicious cyber activities,” “persistently contest malicious cyber activity in day-to-day competition,” and “defend forward to disrupt or halt malicious cyber activity at its source.”7 Simultaneously, the administration provided new authorities for offensive cyber operations and rescinded PPD-20.8
The shift away from the old approach has begun, but implementing the new strategy across all agencies and departments of the federal government will require a sustained effort. For now, the administration continues to rely primarily on sanctions and indictments to impose costs on malicious cyber actors. Over the past two years and coinciding with complementary Department of the Treasury sanctions, the Department of Justice has unsealed indictments against dozens of Chinese, Russian, Iranian, and North Korean intelligence operatives and hackers. In some cases, the Justice Department accused these governments of sponsoring the operations. However, since these operatives are usually beyond the physical reach of U.S. law enforcement, the indictments have rarely led to arrests.9

Cyber warfare operators serving with the 175th Cyberspace Operations Group of the Maryland Air National Guard on December 2, 2017 at Warfield Air National Guard Base in Middle River, Maryland. (U.S. Air Force photo by J.M. Eddins Jr.)
Assessment
The Trump administration has sensibly moved to broaden U.S. cyber policy beyond its previous emphasis on law enforcement actions, which have, at best, an unclear effect on hostile nation-state decision-makers who sponsor and authorize operations. In support of a robust cyber strategy, however, sanctions and law enforcement activities do expose the extent of malicious cyber activity. According to former Assistant Attorney General John Carlin, the indictments themselves also “rais[e] the cost of an attack by promoting vigilance against a named attacker.”10
The uptick in indictments and sanctions has also corresponded with a more creative use of government authorities to punish those responsible for, or benefiting from, malicious cyber activity and to harden federal and civilian infrastructure. The Department of Homeland Security issued a Binding Operational Directive in September 2017 requiring federal agencies to remove all of Russia’s Kaspersky Lab products from their systems over concerns that Moscow uses the company to infiltrate U.S. networks.11 Congress then passed bills banning the government from using Kaspersky products and from procuring goods that use Chinese telecommunications equipment as essential components. The Department of Commerce broadened the pressure on China over intellectual property theft by banning all U.S. exports to semiconductor producer Fujian Jinhua Integrated Circuits, who was responsible for stealing trade secrets from Idaho-based Micron Technology, which produces critical computer components for American cyber, national, and economic security.
The Committee on Foreign Investment in the United States (CFIUS) meanwhile blocked a merger between American and Singaporean companies over concerns that this would harm U.S. innovation in 5G service and allow companies with connections to the Chinese military and intelligence to create the equipment underpinning next generation internet technology. The Federal Communications Commission (FCC) also prohibited federal subsidies for broadband providers that use Huawei equipment. The Trump administration has wisely shared its concerns about Huawei with allies who have begun issuing their own warnings about the company and excluding it from projects.
While it is too early to assess the effectiveness of the Trump administration’s new National Cyber Strategy, the document has received rare bipartisan praise. The new approach has the potential to be an effective, proactive strategy accompanied by new offensive authorities. Former National Security Council Cybersecurity Coordinator Rob Joyce – whose departure from the National Security Council caused lawmakers and experts to raise concerns that the White House lacked sufficient cyber expertise – called the replacement of PPD-20 “a thoughtful rewrite.”12 In October 2018, CYBERCOM reportedly launched its first operation under these new authorities, alerting Russian cyber operatives that the U.S. military was tracking their activities to deter Moscow from interfering in the midterm elections.13
While it is too early to assess the effectiveness of the Trump administration’s new National Cyber Strategy, the document has received rare bipartisan praise. The new approach has the potential to be an effective, proactive strategy accompanied by new offensive authorities.
The Trump administration has also been more forward leaning in its public attribution of cyberattacks, including working with its allies to call out Russia for the 2017 notPetya malware and North Korea for the 2017 Wannacry ransomware attacks. These public statements are important for correcting misconceptions about the inability to positively attribute cyberattacks, and as a first step to imposing consequences.
One urgent issue to address is the president’s refusal to consistently accept the U.S. intelligence community’s assessments of Russian cyber operations during the 2016 presidential election. The politicization of the investigation into Russia’s cyberattacks and cyber-enabled information operations undermines the bipartisanship necessary to implement effective responses to cyber vulnerabilities not only in U.S. election systems, but across all critical infrastructure.
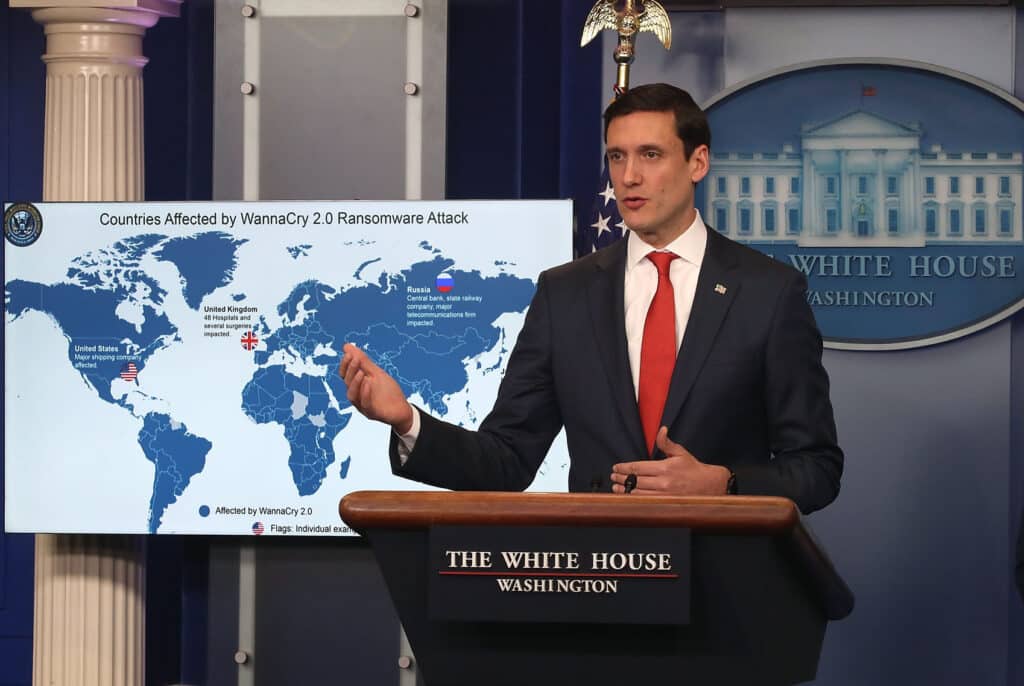
Tom Bossert, former White House homeland security advisor, briefs reporters about the WannaCry cyberattack. (Photo by Mark Wilson/Getty Images)
Recommendations
- Target those responsible for, or benefiting from, malicious cyber operations. The Trump administration should continue to sanction and disable the financial and business networks supporting malicious cyber operations. It should work with foreign partners to dismantle malicious, third party networks within their jurisdictions by sharing information about front companies involved in state-backed cyber operations. Similarly, the administration should create a watch list of software companies it believes are acting on behalf of, or being exploited by, adversarial states in ways that pose a national security risk. It should also produce a public list of foreign companies that use cyber infiltrations and other means to steal U.S. intellectual property or have benefited from the use of stolen intellectual property.
- Excise components from authoritarian states engaged in malicious cyber operations from U.S. and allied supply chains. In conjunction with like-minded nations, the Trump administration should create a consortium aimed at identifying potentially nefarious software or hardware providers; circulate confidential red notices on foreign software and hardware of concern; and develop alternative and more secure information technology supply chains that exclude companies from authoritarian states engaged in malicious cyber activity.
- Synchronize cyber defense capabilities and offensive options with allies. In conjunction with U.S. allies, the Trump administration should develop a joint R&D agenda to address common threats; create a joint cyber intelligence center focused on detection of cyber threats and intelligence sharing about cyber anomalies; and create cyber task forces to synchronize defenses and options for offensive operations and to resolve constraints that nations will face in the event of a joint “hot” cyber conflict. Likewise, America should conduct joint cyber war games to demonstrate international resolve and to build and test interoperability with allies. It should also declare that the United States will respond to and defend its allies against significant cyber campaigns.
- Use cyber and kinetic capabilities to impose costs on adversaries. The Trump administration should prepare offensive measures to restrict adversarial cyber operations and disrupt network infrastructure; use cyber-enabled information warfare capabilities to exploit and sharpen divisions between hostile authoritarian regimes and their oppressed populations; hold at risk assets of value to nations that engage in cyberattacks; and develop a suite of forward-leaning kinetic and non-kinetic options to impose overwhelming costs on those responsible for malicious cyber operations. In these endeavors, the administration should work closely with the congressionally mandated Cyberspace Solarium Commission, created to redress a lack of rigorous strategic thinking and interagency coordination of cyber policy.
- Create secure partnerships and interoperability with the private sector. The Trump administration should form secure and trusted partnerships between the intelligence community and private sector to collect and disseminate (with proper source protection) information about threats; share specific, actionable information with the private sector; and advance interoperability, through joint training and exercises, to enable industry to better defend itself.
- Recruit private sector support for U.S. national security goals. The Trump administration should dissuade U.S. technology firms from providing authoritarian governments the means to facilitate censorship and oppression. Rather, it should encourage them to work with the U.S. national security establishment to aid the defense of the nation. Washington should also incentivize companies to publicize breaches so that it can accurately assess the scope of damage from cyberattacks. Finally, the administration should regularly communicate with the public about cyber threats to foster individual citizen resilience.
