July 28, 2021 | Memo
Cyber Hygiene 101 for Small- and Medium-Sized Businesses
Introduction
Industry reports and surveys paint a frightening picture of the cybersecurity landscape for small- and medium-sized businesses (SMBs): Between 2019 and 2020, cyber intrusions increased by 400 percent around the world, while the FBI received up to 4,000 cyberattack-related complaints per day.1 Forty percent of cyberattacks target SMBs, and up to half of all SMBs experience a breach each year.2 In 2020, the total cost of ransomware payments was $350 million, a 311 percent increase from the previous year.3 In 2020, the average cost of repairing a data breach was $2.64 million for companies with fewer than 500 workers.4 A report on critical infrastructure SMBs found that 46 percent of hacked companies lost customers and 59 percent reported losses in daily productivity because of a breach.5 No wonder 60 percent of small businesses go out of business within six months of a cyber incident.6
SMBs are often unprepared to respond to cyberattacks. Nearly two-thirds of SMB CEOs confess that their companies lack an active, up-to-date cybersecurity strategy.7 This report consolidates advice from industry and the U.S. government on cyber best practices. It provides SMBs a high-level overview of how to integrate investments in people, processes, and technologies to mitigate the risk of the most common types of cyberattacks. For a more comprehensive list of industrial cybersecurity standards and technological controls, the Foundation for Defense of Democracies has also released a “Comparison of Cybersecurity Guidance for Critical Infrastructure Sectors.”8
Cyber Hygiene: People, Processes, and Technology
All businesses face a choice when it comes to technology management, cybersecurity, and risk acceptance: Should the company employ a dedicated, in-house security operations center or outsource these tasks to a managed service provider? In general, outsourcing is the cheaper and more practical solution for SMBs. Regardless of who manages security functions, however, businesses have to understand the risks that stem from the combination of people, processes, and technologies, and weigh their tolerance for those risks.
Cyber hygiene entails persistent due diligence and comprehensive due care. Due diligence is the continual evaluation of security practices; due care is the action taken to ensure security. While the practices listed below should help reduce risk, it is equally important for businesses to be ready to adapt to new exploits presented by the adversary. It is worth noting, then, that enterprise cybersecurity is as much about mindset as it is about any single person, process, or product.
People
Cyberattacks cut across the targeted organization, meaning that every employee needs to understand his or her role in preventing attacks. Employees are both the primary line of defense against cyberattacks and often the weakest link targeted by malicious actors. In fact, IBM estimates that human error contributes to 95 percent of security breaches.9 The best technology in the world today still cannot always prevent employees from clicking on a phishing scam or stop security professionals from neglecting to install a critical security update.
Therefore, businesses should train and educate all of their employees on the importance of:
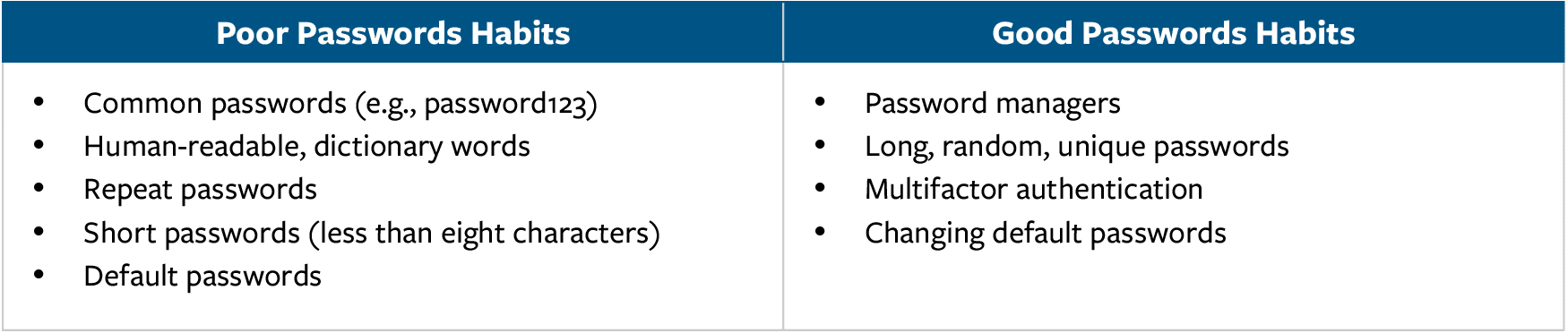
Using Secure Passwords
Reports indicate that 81 percent of cyber breaches involved weak or reused passwords.10 Increasing password complexity and incorporating additional good password habits make it harder for hackers to access accounts, sign into other accounts that share the same password, and establish persistent access to computer networks and devices. Some examples of good and poor password habits include:11
Avoiding Email Scams
According to the cybersecurity company Proofpoint, 88 percent of organizations worldwide experienced spear-phishing attempts in 2019.12 Spear phishing is the act of sending emails containing malware to individuals, often appearing to be sent from a trusted email account. By carefully inspecting the source of the email, or the email sender, and not clicking on suspicious links or download prompts, users can avoid falling victim to email-based scams and attacks.13
Practicing Good Physical Security Habits
In addition to monitoring cybersecurity threats from external sources, SMBs should also be vigilant about physical threats to technology assets.14 A recent study reported that almost 30 percent of businesses do not regularly conduct regular reviews of physical security as part of their cybersecurity practices.15 Employees should be reminded never to leave a computer unlocked or unattended in a public setting.
Updating Software
In a 2019 survey, 60 percent of respondents reported breaches as a result of “unpatched” software for which a patch was available for download.16 Employees should turn on automatic updates where possible and follow guidance from system administrators to ensure updates are safely incorporated into the network environment.17 Additionally, employees should not download software from unknown sources and should verify the update’s authenticity with network administrators before proceeding with the download.
Practicing Safe Browsing
When possible, employees should avoid using public Wi-Fi, which attackers can use to steal passwords or company information.18 When employee use of public Wi-Fi is unavoidable, the businesses should provide a virtual private network (VPN) to encrypt traffic. Additionally, any URL can potentially be used to install malware on a device, so employees need to be careful not to browse untrusted websites and should never disclose passwords over unsecure sites. Browsers such as Google Chrome, Mozilla FireFox, and Microsoft Edge warn users that a website is unsecure by placing an open lock by the URL.
Practicing Safe Social Media Habits
Social media can provide hackers with a significant amount of information, including names, birthdays, spouse and pet names, and places of employment. Given that much of this information is often used to create usernames and passwords, it is highly valuable to hackers. By avoiding the disclosure of personal information over social media and using password managers to increase password complexity, employees can make it more challenging for hackers to access their accounts.
Backing up Data
The recent uptick in ransomware attacks has shown that a failure to back up data can significantly impact a company’s ability to withstand a cyberattack. Regularly backing up files and programs, either through cloud services or through physical hard drives, will facilitate recovery efforts from cyberattacks such as ransomware.19 For larger companies, sophisticated network configuration can render ransomware ineffective.
Processes
A number of frameworks provide high-level ways of ensuring good cybersecurity. These include the National Institute of Standards and Technology’s (NIST’s) Cybersecurity Framework,20 the Center for Internet Security’s Security Controls,21 and the International Organization for Standardization’s 27001 document,22 as well as industry-specific security frameworks.
Every framework consists of a set of “controls,” which are processes or best practices to secure an organization’s assets. These controls can be grouped into methods used to plan for, protect against, detect, respond to, or recover from attacks. Organizations should have clear policies and procedures on cybersecurity. These policies should include designating people in charge of tasks to oversee a set of predetermined steps to be taken throughout the response and recovery process.
Anticipating and Preventing Attacks
To plan for attacks and anticipate threats, companies should conduct threat modeling.23 This entails analyzing a company’s digital infrastructure, identifying threats, ranking which threats are most important, and determining countermeasures.
Analyzing a company’s infrastructure means breaking down a network and understanding how each individual section operates. With the network’s architecture in mind, businesses can examine every section of it and identify weaknesses as part of a systematic vulnerability assessment.24 The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency provides free scanning and assessments to most businesses upon request.25 Penetration testing (a term often used synonymously with “red teaming”) is the practice of stress testing a system by utilizing a dedicated team to attempt to break into the system or exploit potential vulnerabilities. This testing can further identify weaknesses in the network.26
Businesses can also participate in information sharing schemes to better understand recent developments in the threat landscape. The U.S. government promotes membership in Information Sharing and Analysis Centers (ISACs) and Information Sharing and Analysis Organizations (ISAOs). These institutions allow firms in similar sectors to collaborate and share information about relevant threats. ISACs are geared toward larger businesses with in-house cybersecurity defense capabilities. ISAOs are more suitable for small businesses but may not provide as frequent or high-quality information.27
Having identified potential threats, teams should evaluate the costs of improving defenses. The reality of cybersecurity for SMBs is that there are more threats than an SMB can feasibly defend against. Therefore, the threat modeling framework is a tool to conduct a cost-benefit analysis of threats so an organization can prioritize where to spend its resources.
Detecting Threats
Network administrators need to know as soon as possible when their company has been hacked. A 2020 IBM report found that the average breach goes undetected for 207 days. The report also found that detecting and containing a breach in under 200 days saved the hacked organization $1.12 million on average.28 Businesses should set up tools to detect suspicious activity, especially around high-priority assets. For instance, any changes to sensitive files should be logged and flagged for network administrators.29
Meanwhile, employees throughout an organization should know the common signs of a cyberattack. These include unexpected installations on a device; frequent browsing redirects or pop-ups while browsing the web; changed or broken passwords; and disabled anti-malware, task manager, or registry editor programs.
Responding to Threats
Based on the threat modeling’s results, SMBs should establish protocols for reacting to attacks. All employees should know the protocol for how to report and take initial steps when they become aware of a breach. Each attack demands a slightly different response, but the short-term response to a cyberattack generally involves isolating the affected parts of the system, revoking the access or privileges of compromised users, purging the hacker from the system, and alerting law enforcement and any affected parties.30 While there currently is no national breach-notification law, states have their own data-breach notification laws, and regulated industries may have additional reporting requirements. Accordingly, SMBs need to develop procedures and policies in line with these requirements.
Recovering From Attacks
On the software side, the most common step toward recovery is restoring computers to a previous backup. Online guides can provide instructions on how to restore prior working states.31 These instructions are especially helpful in the event of a ransomware attack.
Recovering from business interruption is more complicated. Cyber insurance is becoming increasingly common for businesses of all sizes, but SMBs have still been slow to purchase cyber insurance.32 A 2020 study found that more than half of all SMBs lack cyber insurance despite the prevalence of cyberattacks affecting them.33
A recent Government Accountability Office report noted that while demand for cyber insurance policies has continued to increase year over year, the cost of insurance premiums increased 10 to 30 percent in the third and fourth quarters of 2020.34 The increase in premiums is reportedly attributed to higher losses from the increasing number of cyberattack insurance claims. The increase in price has effectively shifted cyber insurance policies from an affordable $1,000 investment for a basic policy to a price that is likely out of reach for some SMBs.35 Even if affordable, these basic insurance policies may not provide coverage for revenue lost while fixing a breach.36 Needless to say, cyber insurance is not a substitute for other best practices.
Technology
There is no single software suite that will work for every business. Businesses need to weigh their specific needs, risks, and constraints when purchasing technologies. Businesses must also ensure their employees can easily adapt a given technology to their work. This means clear company policies, easily installable software, and basic training so employees know how to use the tools and products provided. For example, a password manager is useless if employees never use it or if they use it only to fill in the same password over and over again. While not exhaustive, the following list provides 12 technologies that can assist SMBs in their cybersecurity efforts.
Password Managers, Single Sign-On, and Multi-Factor Authentication
Password managers generate random, hard-to-guess passwords.37 They require an employee to remember only a single secure password to access the full collection of advanced passwords for all his or her accounts. Most modern web browsers have built-in password managers that can generate and store hard-to-guess passwords.
Single sign-on is a similar solution in which employees need to log in only once to access an entire suite of apps for a set period of time.
Multi-factor authentication means requiring verification from a second “factor,” which may be either a separate login step or a physical token.38 Even if attackers guess a password, they will still need to get access to the second factor, which makes it harder to gain unauthorized access to the targeted network.39
Access Control
Most networks have some form of built-in login or access-control system to keep out unauthorized users.40 Businesses should configure their login systems so that users cannot use weak passwords and will get locked out after a certain number of failed attempts. Accounts and devices should be configured to lock automatically after a certain period of inactivity. Companies should also consider configuring their access-control systems to apply other security measures, such as preventing logins from foreign countries or unusual locations. Finally, employees should have access only to the information they need for their jobs. For instance, most employees should not be able to access or alter sensitive customer information.
Most often, a dedicated network administrator determines how to configure the network. Therefore, it is especially crucial that network administrators practice good cyber hygiene, as an attack that compromises an administrator potentially gives the attacker control over the entire network. Administrators should use their administrator accounts only when necessary; they should have a separate account for all other functions, such as browsing the web.
Firewalls, Intrusion Prevention Systems, and Endpoint Protection Platforms
Most networks should have comprehensive schemes to prevent malicious cyber activity from ever reaching a computer or device (known as an endpoint). At a minimum, this means employing a standard firewall that filters out malicious traffic.41
Many companies employ multiple layers of protection, such as an intrusion prevention system42 underneath the main firewall.43 These systems provide a second line of defense in filtering out malicious traffic and can alert administrators to any suspicious activity.
Endpoint protection platforms serve a similar function by scanning files and checking them against extensive, externally maintained threat databases to prevent malware from ever reaching the computer.44
The precise differences between firewalls, intrusion prevention systems, and endpoint protection platforms are less important than the general need for products that can filter out malicious traffic. As businesses grow and encounter more sophisticated attacks, their endpoint security should also become more sophisticated. However, everyone, from the smallest businesses to individual contractors, should have at least some software to filter out harmful traffic.
Anti-Malware
Malware is short for malicious software, which is specifically designed to damage data or a computer system. It is software used to disrupt computer operations, gather sensitive information, or gain access to private computer systems. Malware typically comes in the form of malicious code hidden in computer systems and is often installed without the knowledge or consent of the computer’s owner, using viruses, worms, or trojan horses. Anti-malware is software that scans incoming files and downloads to prevent a user from being infected.45 It should regularly scan the computer to find any malware that slipped past that first line of defense. Anti-malware software uses techniques such as signature-based detection, behavior-based detection, and sandboxing to protect systems from malicious software. The value of anti-malware applications goes beyond simply scanning files for viruses. Anti-malware programs can also detect advanced forms of malware and offer protection against ransomware attacks.
VPNs and Zero-Trust
Many companies use VPNs to encrypt and help authenticate remote traffic.46 VPNs operate by creating a tunnel between a user and the network. Instead of having data go directly from the user to the end location, VPNs act as a middleman, encrypting traffic between the two parties to make it harder for attackers to intercept or impersonate a user.
However, cybersecurity experts increasingly see VPNs as insufficient protection against unauthorized traffic. They instead recommend building zero-trust networks, which do not give automatic access to the network merely through a VPN. Zero-trust networks operate under the mantra “never trust, always verify.” No user or device is trusted by default, meaning that even within a network, users must constantly verify their identity.47 This paradigm helps isolate and identify breaches but is still a relatively new phenomenon. Therefore, transitioning toward a zero-trust network will likely take time for many organizations.
Data Loss Prevention
Data loss prevention (DLP) software is the opposite of a firewall: It ensures sensitive data does not leak out into the broader internet.48 Many cybersecurity software providers (such as McAfee, Norton, et cetera) can bundle DLP, firewalls, data sanitization, and anti-malware software all in one. DLP software monitors business-critical data and identifies violations of policies defined by the SMB. If violations are identified, DLP software provides alerts and other protective actions to prevent end users from accidentally or intentionally sharing data that could put the SMB at risk. DLP software and tools monitor and control endpoint activities, filter data streams on business networks, and monitor data in the cloud to protect data at rest or in motion.
Email Protection Systems and Anti-Phishing Tools
Most email providers supply baseline spam filtering either by default or for purchase. Adding additional software on top of what the email provider offers can mitigate phishing attacks.49 Specifically, email protection systems should have:
- Sender Policy Framework: Limits the number of internet protocol (IP) addresses using a business’ domain, to prevent email spoofing.
- Domain Keys Identified Mail: Uses a digital signature to ensure no one tampers with an email after it is sent.
- Domain-based Message Authentication Reporting and Conformance: Verifies if a sender is legitimate, and manages the policy governing how to handle illegitimate emails.
Data Sanitization Tools
File recovery software can retrieve files that are merely deleted from a disk or drive. Companies can use a variety of free and paid tools to clean or purge sensitive data more securely so that the data do not fall into the wrong hands.50 If all else fails, companies should have a policy of physically destroying hardware that previously housed sensitive material. Most cloud providers will automatically sanitize deleted data, but it is important to check their policies.51 Furthermore, for cloud services that can be synced to local computers, deleting the cloud copy does not guarantee that the local copy has also been securely deleted. Therefore, companies should avoid syncing highly sensitive data to multiple local hosts if that data may need to be deleted quickly.
Security Information and Event Management Systems
To properly monitor a network and detect breaches, IT professionals should employ a security and event management (SIEM) system.52 This software logs activity across the network. Attackers looking for persistent access to a network will often attempt to erase log files because their activity may appear in the log as anomalous activity. Thus, it is important that SIEM systems are configured to mitigate attackers’ ability to cover their tracks.53
DNS Security
The domain name system (DNS) translates human-readable domain names (such as www.example.com) into computer-friendly numeric addresses (such as 12.345.67.890). Compromising the DNS opens the door to a variety of attacks, from stealing information to impersonating sites to redirecting users to malicious sites. Within an organization, DNS compromises pose a threat to any device connected to both the internet and the internal network.
DNS Security Extensions (DNSSEC), DNS over HTTPS (DOH), and Protected DNS (PDNS) provide enhanced protections against common DNS attacks while browsing the web. DNSSEC uses encryption to ensure that DNS queries are not altered (meaning no one can maliciously redirect traffic unbeknownst to the user).54 DOH also uses encryption to secure the DNS, but this time to prevent hackers from spying on DNS queries.55 PDNS works by configuring a policy for detecting malicious IP addresses to prevent users from landing on a malicious site even after the URL has been translated from a human-readable domain into a computer-readable address.56
DNS Registrars
Companies with websites need to ensure that users of their sites are not subject to DNS attacks. Normally, companies purchase domain names through a domain name registrar. While purchasing a domain name can be very cheap for some providers, businesses should consider investing in enterprise-level registrars that can guarantee better security. These providers offer more comprehensive protection against misspelled URLs and are better at protecting against common DNS attacks.57
Secure Socket Layer Certificates
Secure Socket Layer (SSL) certificates enable encryption between a website and the user, making it more difficult for hackers to steal private customer data passed over the web. These certificates also verify a website’s identity and ownership to users. In most browsers, sites with SSL certificates have a closed padlock as well as text notifying the user that the site is secure. It is in an SMB’s best interest to obtain an SSL certificate so that customers visiting its website do not turn away after receiving a message that the site is not secure. SMBs can obtain an SSL certificate by going through registration and verification by a certificate authority.58
Conclusion
SMBs will continue to face constant threats from malicious cyber activity. Meanwhile, the trend toward remote work and digitalization of operations will only further expand the attack space for businesses. However, according to a 2021 survey, only 18 percent of SMBs were confident that they are prepared for a cyberattack.59 Going forward, efforts to mitigate risk must match the threat. Whether an SMB relies on a managed service provider or conducts its own security efforts, cybersecurity is a critical challenge that requires the attention of the company’s senior leadership. Successful cybersecurity requires investments across three lines of effort: people, processes, and technology. The list of solutions above is not all-inclusive, but a cyber hygiene plan rooted in these recommendations stands a greater chance of success in an increasingly risky cyber environment.